Portfolio
A fusion of public work and classified excellence.
We’ve built, secured, recovered, and transformed a wide range of digital ecosystems. Some clients are proud to showcase their journey. Others require total discretion. Here, we balance trust with proof — sharing what we can, redacting what we must.
Verified Public Projects
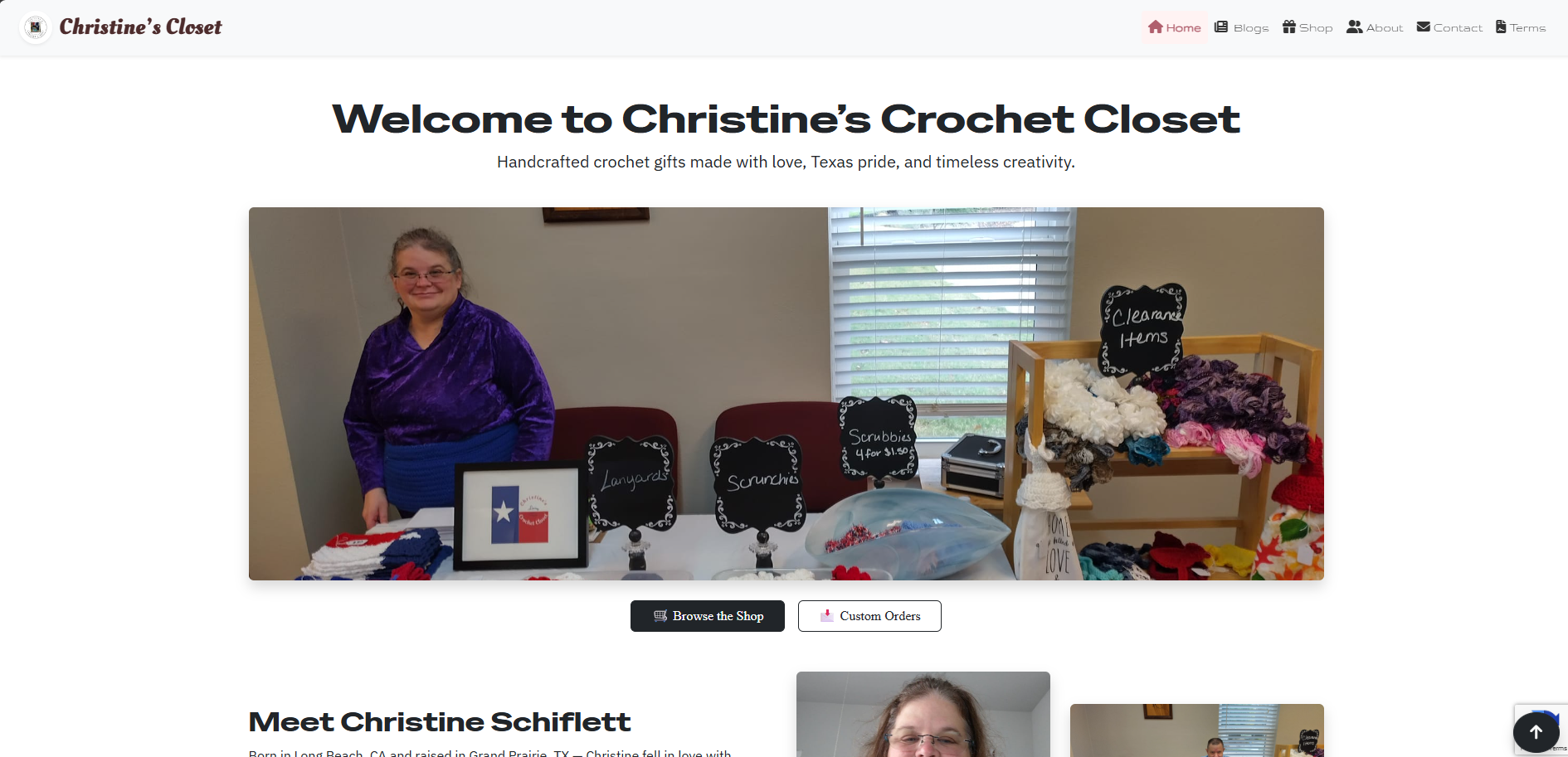
Christine’s Crochet Closet
Custom e-commerce platform with newsletter automation, CRM integration, and admin inventory control — built with security-first PHP backend and AJAX-driven UI.

B1 Technologies (EZ-Rater)
Designed a fully working EZ-Rating software for a local Texas commercial based insurance company to help them retrieve multiple quotes at a time.
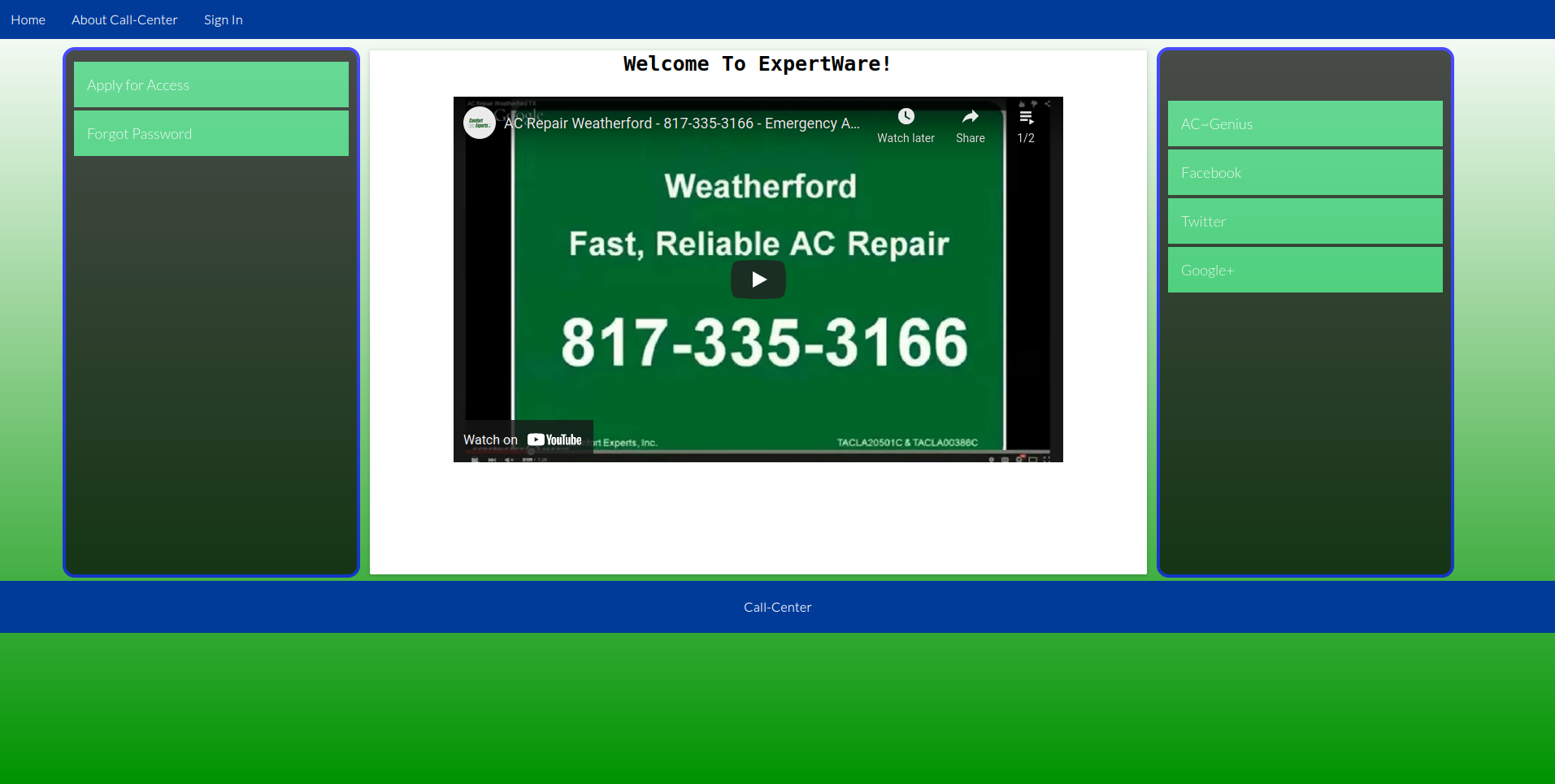
ExpertWare
Designed a fully working back-end call-center operation using Ruby on Rails and PostgreSQL Database for a reputable AC Company in Texas.
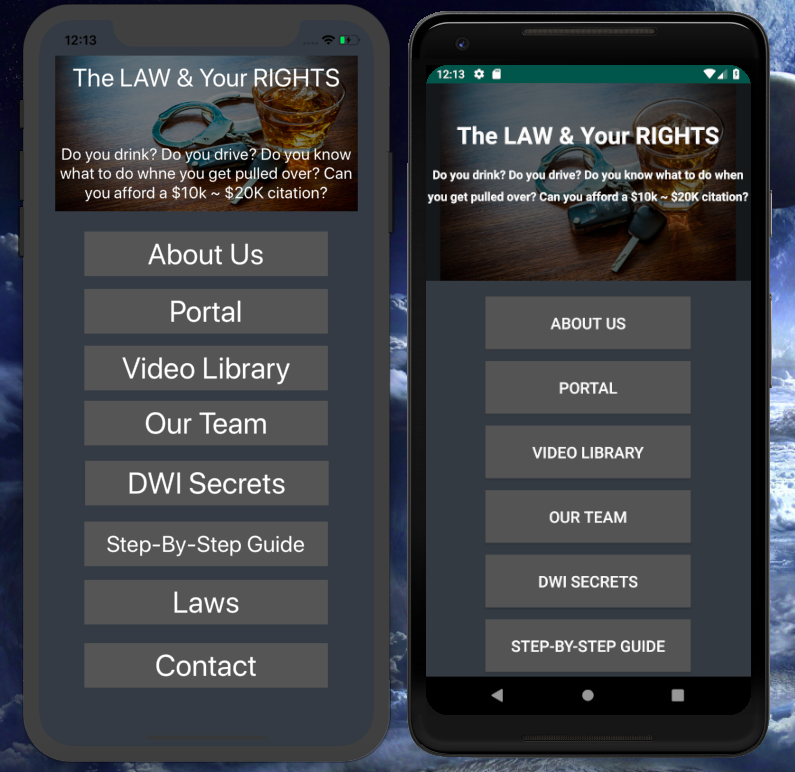
DIY/DWI
A mobile application for a DIY/DWI Lawyer to give to their clients for recording videos, images, and taking notes directly on their phones.
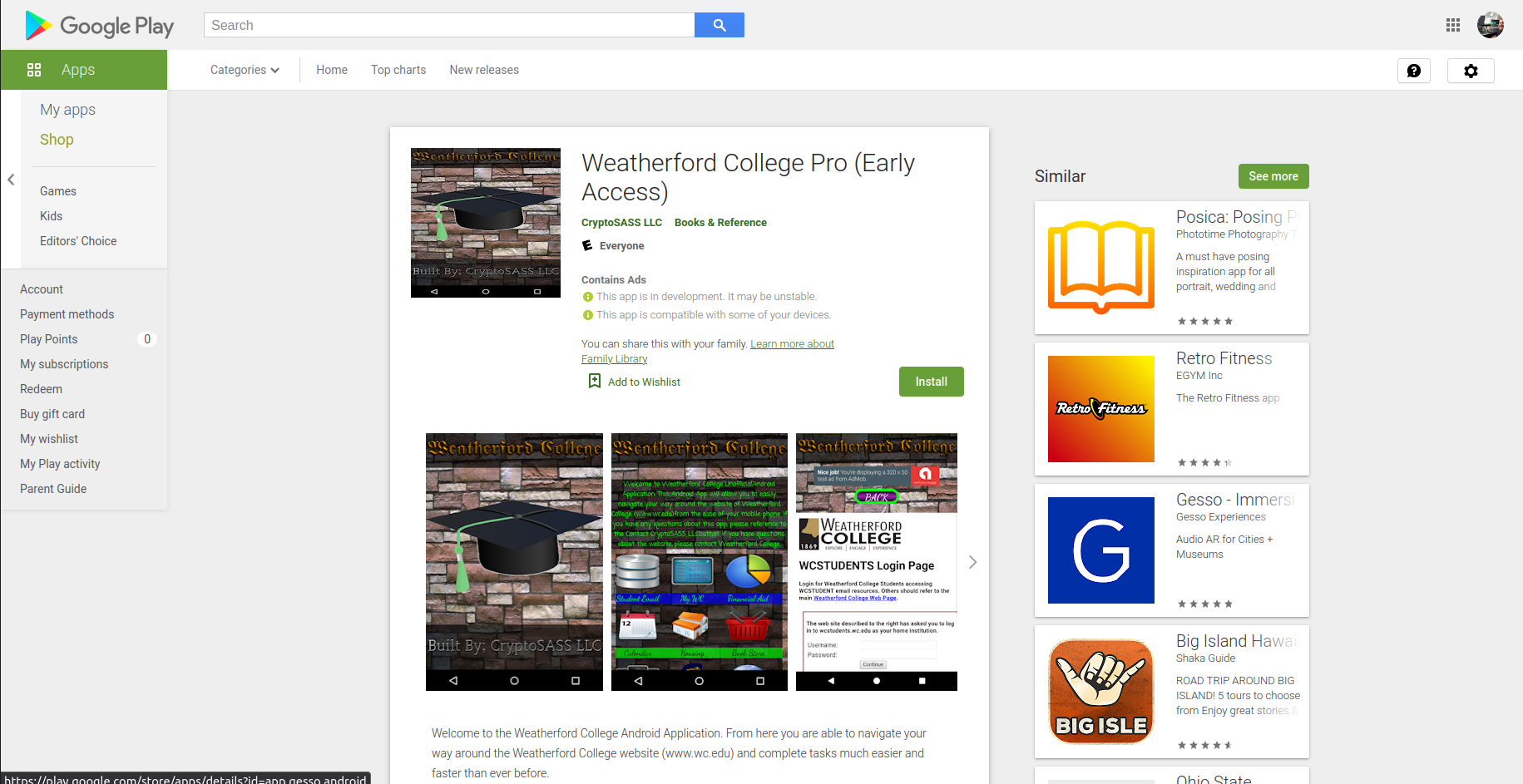
Weatherford College Android App
Designed for student navigation: class schedules, push notifications, secure logins, and real-time campus updates. Google Play-integrated release pipeline.
[REDACTED] Cybersecurity Engagements
Due to client confidentiality and risk mitigation, identities and environments are concealed. These cases reflect real-world impact across sectors including FinTech, SaaS, education, and healthcare.
[REDACTED] – FinTech Payment Platform
During a responsible audit, we uncovered exposed API tokens capable of initiating unauthorized transactions. Full exploit was proofed and mitigated within 24 hours. Client revised lifecycle key protocols and credited Grey Node Security in their SOC2 audit review.
[REDACTED] – Messaging App Platform
Identified two independent 2FA bypass vectors resulting in account takeover. Findings submitted to internal bug bounty program and patched within 72 hours. Company overhauled MFA architecture as a result.
[REDACTED] – E-Commerce SaaS Environment
Demonstrated privilege escalation via token interception in password reset flow. Reported responsibly. Vendor reinforced access control headers and session token scope validation.
[REDACTED] – Healthcare Data Broker
Discovered outdated Apache stack leaking internal endpoint logic. Penetration test resulted in hardened middleware, access control lists, and third-party API proxying with WAF rules implemented.
Over a Decade of Operational Excellence
From code to compromise recovery, from initial deployment to incident remediation — Grey Node Security has delivered success stories silently, professionally, and effectively across the map. Our results are real. Our clients are protected. Our mission is trust.
Begin a Confidential Consultation